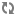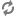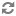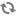New button [Set layer] has been added to HIS toolbar. It opens side panel where user could specify visibility of Object Overlay and Redlining layers. For both type of overlays either all layers could be visible or one of them.
After choosing object with document linked to it we have new button (just under Print Preview, the one with printer icon). To make quick print you just have to click the button and on the new Internet Explorer window choose on with printer you want to print.
Configuration
Quick Print parameters are set in HDocASP.ini. Here are the params and possible values:
QuickPrintTemplate = "";
template names,
QuickPrintOrientation = "P";
"P" for portrait orientation,
"L" for landscape orientation,
"P" portrait is set if not recognized value was writen,
"P" portrait is set if ther is no QuickPrintOrientation param in .ini file.
QuickPrintScalingMode = "FD";
"SV" scale view,
"MV" match view,
"FD" fit drawing,
"MD" match drawing,
"SV" scale view is set if not recognized value was writen.
"FD" fit drawing is set if ther is no QuickPrintScalingMode param in .ini file,
QuickPrintResolution = "600";
"150" dpi,
"300" dpi,
"400" dpi,
"600" dpi,
"300" dpi is set if not recognized value was writen,
"600" dpi is set if ther is no QuickPrintResolution param in .ini file.
New button [Copy selected spots] has been added to Measure toolbar, before Insert Length and Insert Area Measurements. To copy selected spots to measurement layer select desired spots from overlay drawing and activate the Copy button. Selected entities are cloned and pasted to measurement drawing, selected to further editing. Cloned entitities can be moved and reedited as desired.
The same functionality can be used to duplicate entities selected from measurement drawing.
Quick Search functionality is available for use In Object Properties window.
Search is performed on single object class / field according to configuration. Suggested result can be selected either by mouse click or by navigation with arrows and pressing Enter.
Quick Search needs to be configured in the INI file prior to use.
Configuration
Default values are used when not specified in INI file. Values for 5th, 6th, and 7th parameter must be provided and do not have default values (Parameters are not validated, if there is a spelling error search will not return any results!).
If any of the parameters is out of specified bounds, a warning message is displayed and Quick Search is disabled automatically.
Sample INI section:
[Configuration] QSearch_Enabled=1; QSearch_Match=5; QSearch_PageSize=5; QSearch_Hierarchy='HDocHierarchyDefinition'; QSearch_ObjType='Buildings'; QSearch_Field='Building_Address';
HIS application code has been improved for compatibility with W3C web standards. From now on user could access HIS application from within other browsers than Internet Explorer.
1. To use LDAP server as authentication server create file name ldap.conf and put this file in directory where HDocCfg.DAT file exist
Syntax of this file is identical to ldap.conf file used in UNIX ( Linux ) type operating system.
2. When this file must be located in other place than default, put it location in following key in HDocCfg.DAT file
[Ldap] Conf=…………
3. HyperDoc works with LDAP server when “Proprietary User List” is selected – to select this mode start HDAmin and next use menu “User List Mode”
Configuration
HyperDoc read following values from HDocCfg.DAT file
[Ldap] Conf= Authenticationflags=
Key named Conf is used to specify location of ldap.conf file, when this key is empty than we search for ldap.conf file in the same folder where HDocCfg.DAT file is located.
Key named Authenticationflags is used to specify additional values passed to ADSDSOObject object.
More about possible values and proper usage of this value is found on microsoft.com web pages
Default value for authenticationFlags is 0
Set m_oConn = CreateObject("ADODB.Connection")
m_oConn.Provider = "ADSDSOObject"
m_oConn.Properties("ADSI Flag") = authenticationFlags[Ldap] Authenticationflags = 0
Values for authenticationFlags used in ADsOpenObject function
typedef enum {
ADS_SECURE_AUTHENTICATION = 0x1,
ADS_USE_ENCRYPTION = 0x2,
ADS_USE_SSL = 0x2,
ADS_READONLY_SERVER = 0x4,
ADS_PROMPT_CREDENTIALS = 0x8,
ADS_NO_AUTHENTICATION = 0x10,
ADS_FAST_BIND = 0x20,
ADS_USE_SIGNING = 0x40,
ADS_USE_SEALING = 0x80,
ADS_USE_DELEGATION = 0x100,
ADS_SERVER_BIND = 0x200,
ADS_NO_REFERRAL_CHASING = 0x400,
ADS_AUTH_RESERVED = 0x80000000
} ADS_AUTHENTICATION_ENUM;
HyperDoc read following values from ldap.conf file:
# Your LDAP server. #host 127.0.0.1 # The port. Optional: default is 389 or 636 when ssl is on. #port 389 # Another way to specify your LDAP server is to provide an url with server name. #uri ldap://127.0.0.1/ #uri ldaps://127.0.0.1/ # Netscape SDK LDAPS #ssl_on # The distinguished name of the search base. #base dc=example,dc=com # The distinguished name to bind to the server with. Optional: default is to bind anonymously. #binddn cn=proxyuser,dc=example,dc=com # The credentials to bind with. Optional: default is no credential. #bindpw secret # Filter to AND with uid=%s #pam_filter objectclass=account # The user ID attribute (defaults to uid) #pam_login_attribute uid # Group member attribute #pam_member_attribute uniquemember # Object mapping for following object: posixAccount, posixGroup #nss_map_objectclass posixAccount user #nss_map_objectclass posixGroup group # Attribute mapping for following attributes: objectClass, gidNumber, pam_login_attribute, pam_member_attribute #nss_map_attribute gidNumber sAMAccountName
Important note:
only one LDAP server could be specified in used ldap.conf (if there are more it doesn't work),
to enable ldab authentication logging in HyperDoc please update ini file with: [TSL Diagnostics] LogLDAP=1
HIS requirements to work with LDAP:
1. Correct ldap.conf ( if LDAP is AD type it shoul consist binddn i bindpw of person who have rights to access AD base)
2. Correct HDocCfg.DAT ( consisting of Login and password to SQL Server)
3. Correct HdocASP.ini
[ODBC Settings] ProprietaryUserListMode=1 UserName=…….. Password=……
Please note: UserName and Password should be for proper account in LDAP ! (Password is checked in LDAP server) This account should have HIS administrators usual rights
Replicator Add-in code has been optimized for faster work and from now on users could use it to replicate following objects: print templates (with icons if applicable), presentations definitions and symbol library file. To enable those possibilities please add following options to your replication profile:
Presentations="1" SymbolLibrary="1" Icons="1" PrintTemplates="1"
(please refer to ReplicationProfiles.txt for more information on replication profiles)
Please note that in ini files for source and destination databases in General section, parameters: IconPath and TemplateDirectory should be specified.
Unfortunately in this version there is a limitation: in case of print templates, icon files and symbol libraries in we do not support files stored in a database.
We encourage to use one more replication option which could be defined in a replication profile:
FullParentData="1"
With this option also parent of chosen replicated object will be transfered to server. It could be very useful in case that we want to replicate object from a first level of the hierarchy with a documents connected to a root of a given hierarchy.
In case of replication of large databases we recommend to use incremental replication by parts of the database. It is good practice to restart HyperDoc after dozen of replications (it is to minimize chances of memory problems).
Following HDocASP.ini options in [Configuration] section are important to allow working with redlining drawing on client (these options has been used earlier as well):
// Allow writing (transferring) measurement drawings into redlining drawing layers // For this flag to be effective as 'true', RW licence has to be active write_vectors=true; // when set to 'true' directs client to allow // measurements transfers only to own, private redlining layers upd_priv_redl_layers_only=false;
Essential difference in current implementation is possibility to work on HIS client with entities stored in redlining drawing, which is transmitted to the client in similar way as overlay drawing is.